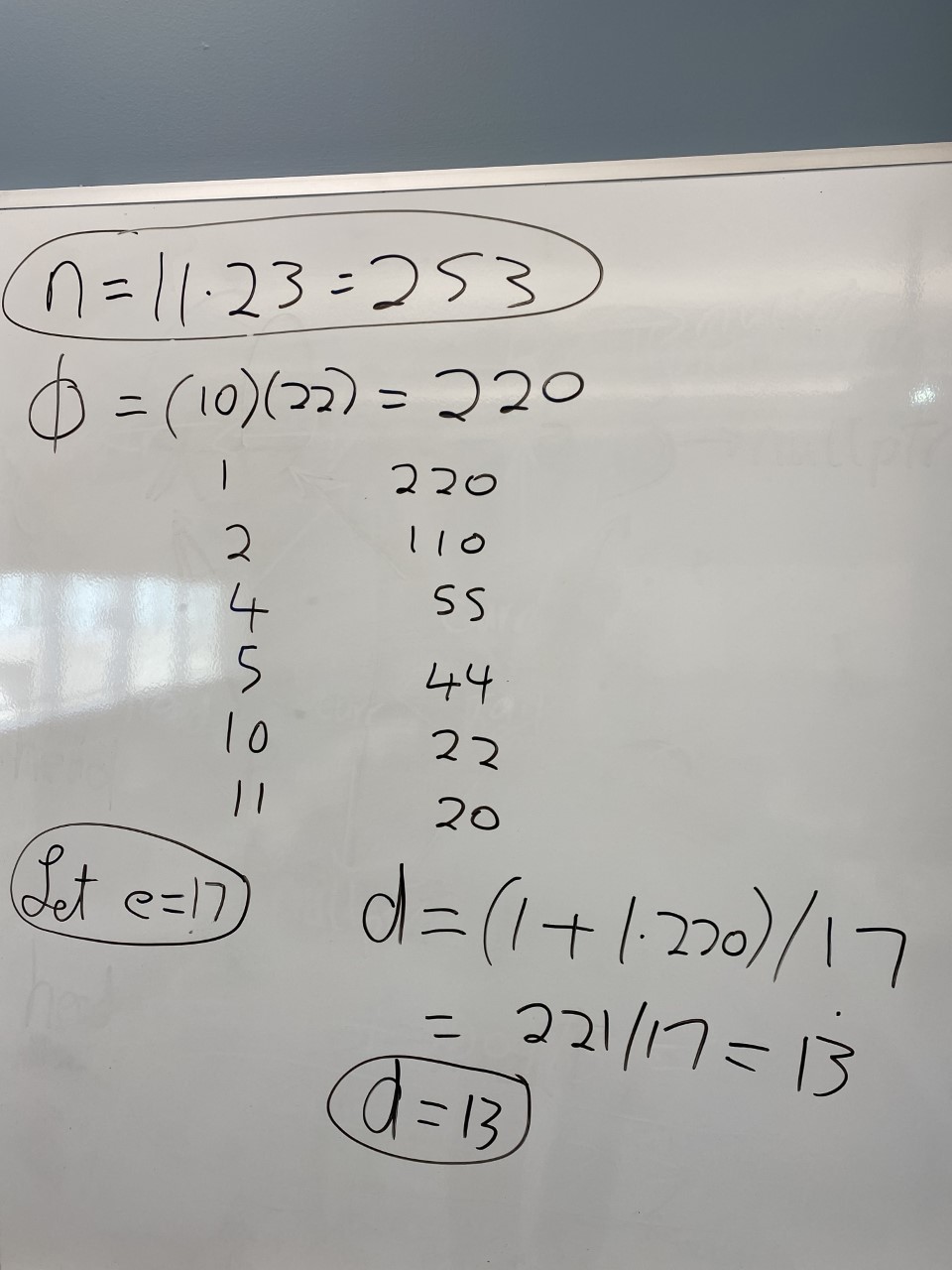
Sample encryption and decryption of data can be seen below:
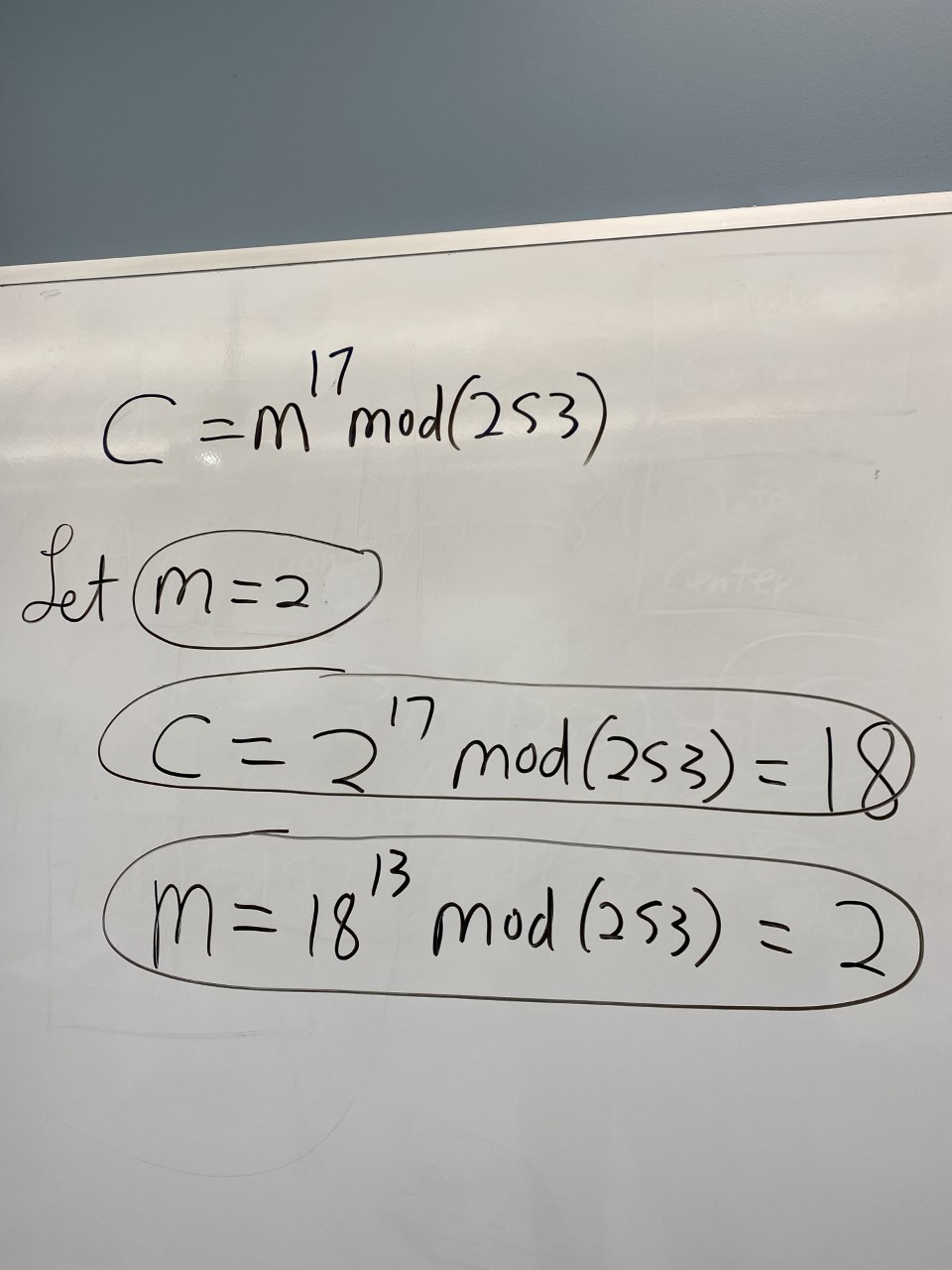
Two processes are going to communicate with each other via UDP INET sockets. The data being passed back and forth will be
encrypted using RSA encryption. We will assume that authentication has taken place and that they will use the same private
key for encryption, and the same private key for decryption. The two prime numbers used in the scheme are:
p=11, q=23.
From these two prime numbers the remaining parameters for RSA (n, phi, e, and d) can be determined.
For RSA encryption,
Sample calculations for n, phi, e and d can be seen below:
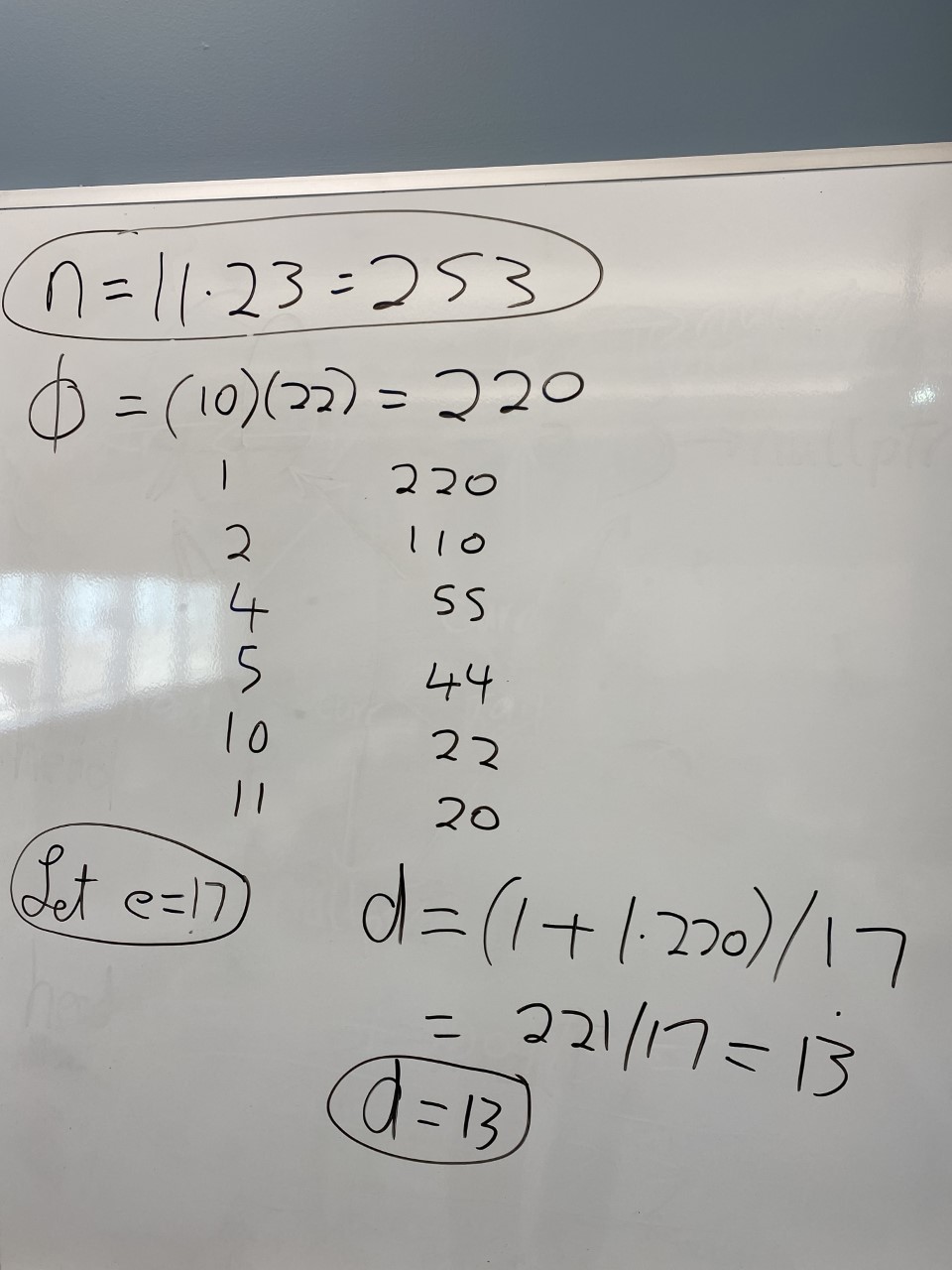
Sample encryption and decryption of data can be seen below:
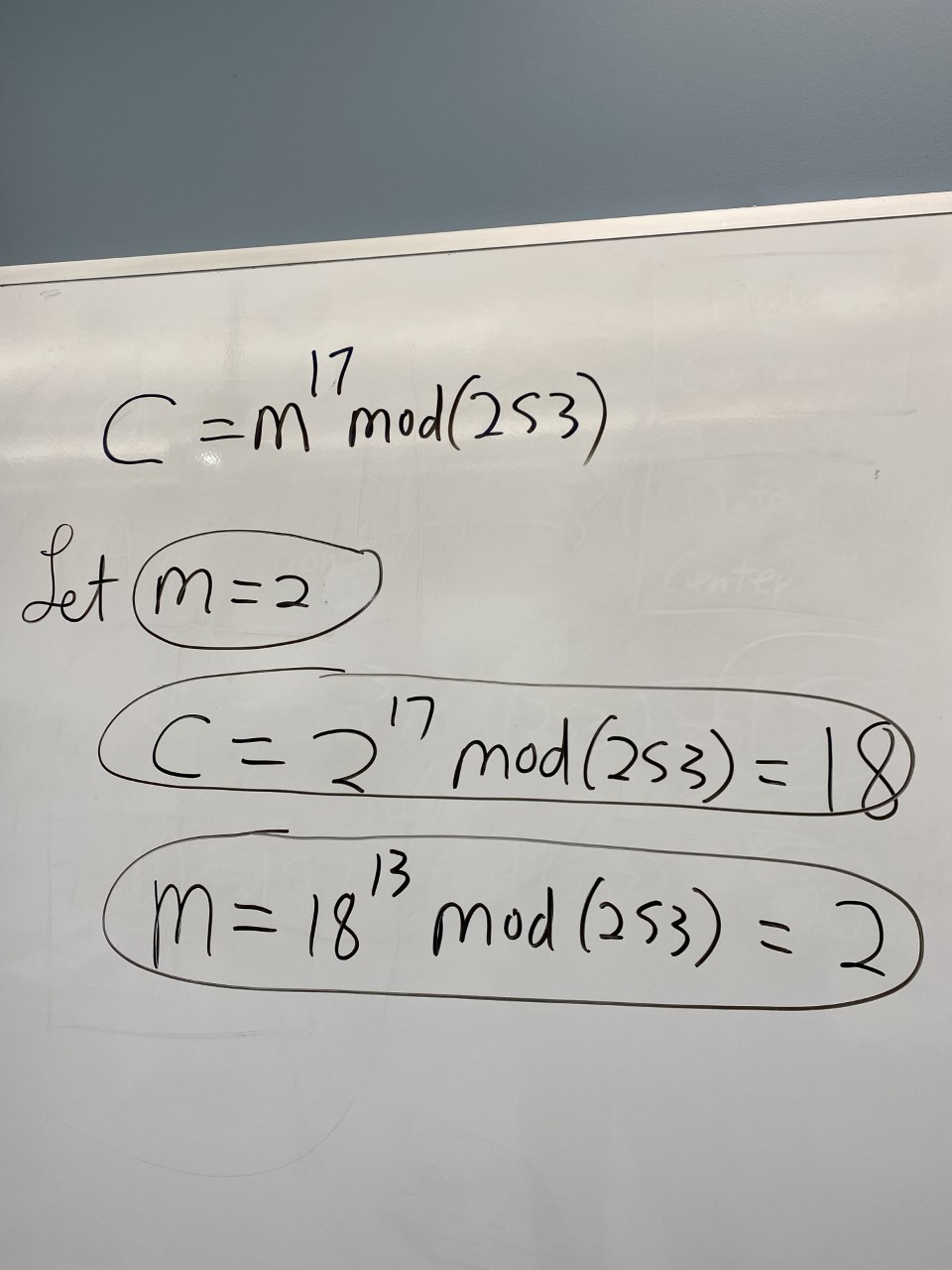
Client 1 is going to pass the following 5 messages to client 2:
"House? You were lucky to have a house!",
"We used to live in one room, all hundred and twenty-six of us, no furniture.",
"Half the floor was missing;",
"we were all huddled together in one corner for fear of falling.",
"Quit"
Client 2 is going to pass the following 5 messages to client 1:
"You were lucky to have a room. We used to have to live in a corridor.",
"Oh we used to dream of livin' in a corridor! Woulda' been a palace to us.",
"We used to live in an old water tank on a rubbish tip.",
"We got woken up every morning by having a load of rotting fish dumped all over us.",
"Quit"
The above is taken from the Monty Python skit
Four Yorkshiremen.
The code for your clients will almost be identical. They can both run on the same machine.
The Makefile as well as skeleton code has been given for the clients. Feel free to change any of these if you wish:
Makefile,
client1.cpp and
client2.cpp.
Be sure to start both processes simultaneously. A sample run is shown below. For client 1:
miguelwatler@ubuntu:~/sep400/Labs/Lab8$ ./client1
p:11 q:23 n:253 phi:220 e:3 d:147
Received: You were lucky to have a room. We used to have to live in a corridor.
Received: Oh we used to dream of livin' in a corridor! Woulda' been a palace to us.
Received: We used to live in an old water tank on a rubbish tip.
Received: We got woken up every morning by having a load of rotting fish dumped all over us.
client1 is quitting...
miguelwatler@ubuntu:~/sep400/Labs/Lab8$
For client 2:
miguelwatler@ubuntu:~/sep400/Labs/Lab8$ ./client2
p:11 q:23 n:253 phi:220 e:3 d:147
Received: House? You were lucky to have a house!
Received: We used to live in one room, all hundred and twenty-six of us, no furniture.
Received: Half the floor was missing;
Received: we were all huddled together in one corner for fear of falling.
client2 is quitting...
miguelwatler@ubuntu:~/sep400/Labs/Lab8$
For the following questions, you might want to read the article: Prime numbers keep your encrypted messages safe — here's how.
QuestionsPlease mail your Makefile, client1.cpp, client2.cpp and answers to the questions to: miguel.watler@senecapolytechnic.ca
NB: My last name is Watler, not Walter.
You will be docked 10% if your lab is submitted 1-2 days late.
You will be docked 20% if your lab is submitted 3-4 days late.
You will be docked 30% if your lab is submitted 5-6 days late.
You will be docked 40% if your lab is submitted 7-8 days late.
You will be docked 100% if your lab is submitted over 8 days late.